While updating our cybersecurity marketing materials at Plante Moran, I met with one of our graphic designers, Amanda Dine, to explain the state of the industry. She took my words and created this image:
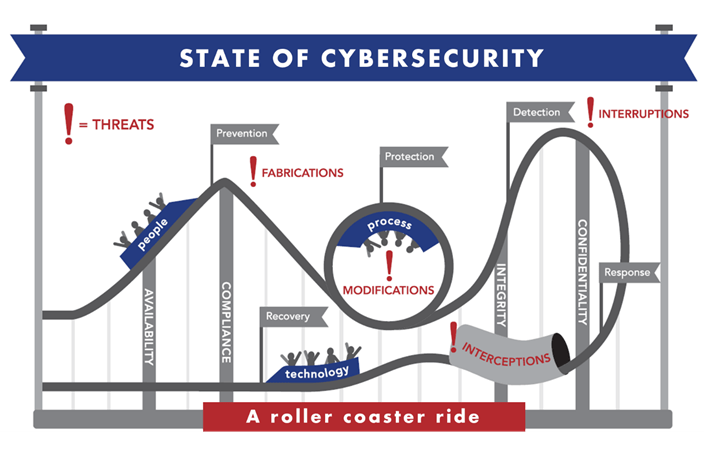
As you can see, she envisioned a roller coaster ride: sometimes you’re up, other times you’re upside down, and sometimes you might even feel like you’re in the dark. It can be really scary and, just when you think the worst is over, the floor can fall out from under you.
I think the designer nailed it. The roller coaster image is a great depiction of the state of cybersecurity. Think about it: over the last 12 months, companies have made significant investments in cybersecurity, yet incidents are increasing and the impact is worsening. Why is that?- Our #1 defense is our #1 weakness
We rely on passwords to grant access to systems and sensitive data — but passwords typically aren’t strong enough and can be easily cracked with online tools. In 2015, after five years of research, professors at Carnegie Melon University released a paper on how passwords are cracked. The report explains the core of the problem is ease of predicting human behavior. For example, it’s common practice to replace the letter “S” in a password with “$.” When people do this, they think they’ve made their password stronger, but cracking tools recognize this behavior and account for it. - Our #2 defense is our #2 weakness
We rely on users to uphold security standards — but users can fall prey to phishing attacks, write passwords down, or provide too much information on social media. We’ve even seen network administrators seek advice from online user groups with detailed descriptions of their company network. Users will continue to be a weak link in cybersecurity.
- Biometric information wouldn’t be stored on corporate or online systems but would reside on the user’s card or phone.
- Security wouldn’t be compromised if the card or phone were lost or stolen because the user’s biometric information would be required to access information.
- An encrypted card or phone is somewhat tamper proof considering it generates a new key code for each use.
I can’t wait for the day passwords and users are no longer our primary defenses against cybersecurity. Once biometrics take hold, we can finally step off of the rollercoaster, as our identities will reside safely with us and not in the hands of multiple corporate and online sources.
This content originally appeared at crainscleveland.com and is part of a special blog series on cybersecurity.





