A comprehensive examination of SOC for Cybersecurity
 In May 2017, a ransomware attack infiltrated the UK’s National Health Services (NHS) network.This attack caused delays in medical procedures and chaos within the affected facilities.The attack, labeled WannaCry, was widespread within the NHS network and could havebeen prevented with proper security updates had they been installed in a timely manner.Global cyberattacks such as WannaCry are becoming increasingly more common. As a result,organizations as well as their vendors, business partners, and other stakeholders are makingcybersecurity risk management a top priority. In response, the American Institute of CertifiedPublic Accountants (AICPA) released the new SOC for Cybersecurity examination to provideorganizations the opportunity to communicate their process for managing cybersecurity threatswith a comprehensive risk management program.
In May 2017, a ransomware attack infiltrated the UK’s National Health Services (NHS) network.This attack caused delays in medical procedures and chaos within the affected facilities.The attack, labeled WannaCry, was widespread within the NHS network and could havebeen prevented with proper security updates had they been installed in a timely manner.Global cyberattacks such as WannaCry are becoming increasingly more common. As a result,organizations as well as their vendors, business partners, and other stakeholders are makingcybersecurity risk management a top priority. In response, the American Institute of CertifiedPublic Accountants (AICPA) released the new SOC for Cybersecurity examination to provideorganizations the opportunity to communicate their process for managing cybersecurity threatswith a comprehensive risk management program.
What is SOC for Cybersecurity?
SOC for Cybersecurity is an independent third-party assessment of an organization’scybersecurity risk management program. SOC for Cybersecurity introduces a set of benchmarksto standardize reporting on the description and effectiveness of an organization’s cybersecurityrisk management program.
SOC for Cybersecurity introduces a set of benchmarks to standardize reporting on the description and effectiveness of an organization’s cybersecurity risk management program.
The organization’s cybersecurity program is a set of policies,processes, and controls to achieve the cybersecurity objectives that protect against the criminalor unauthorized access or attack using electronic data. The framework has been designed tobe specific to the organization’s industry and applicable standards and can follow frameworkssuch as National Institute of Standards and Technology (NIST), Payment Card Industry DataSecurity Standards (PCI DSS), International Standardization Organization and InternationalElectrotechnical Commission (ISO/IEC), or Control Objectives for Information and RelatedTechnologies (COBIT). The framework standardizes the manner by which organizations defineand communicate their cybersecurity objectives and risk management controls designed tomitigate risks.
Use of the assessment
The independent third party can perform a gap analysis to prepare an organization for theexamination or move directly to the performance of a SOC for Cybersecurity examination.
Gap analysis
Independent third parties can use the new set of benchmarks to perform a gap analysis toidentify vulnerabilities within an organization’s cybersecurity risk management program. Thegap analysis can identify controls, policies, and procedures that are not designed to adequatelyaddress risks, as well as, identify risks that are not yet addressed in the cybersecurity riskmanagement program. The organization can design controls and implement remediation ofidentified weaknesses within their risk management program based on the results of the gapanalysis.
SOC for Cybersecurity Examination
Independent third parties examine the design and operating effectiveness of internal controlsin relation to the organization-wide risk management program and how those controls addressthe organization’s cybersecurity and business objectives. A report is issued by the independentthird party with an opinion on the design and operating effectiveness of the controls within thecybersecurity risk management program. The report is available for general use upon issuance.
Description criteria
In order to perform an examination on the design and operating effectiveness of thecybersecurity risk management program, the organization’s management is required to
document and provide an assertion to the description of the cybersecurity managementprogram. The description should be developed according to the guiding principles identified bythe AICPA’s Assurance Services Executive Committee (ASEC) within the description criteria. Thedescription criteria is designed to help organizations define the cybersecurity objectives andthe internal controls that make up the cybersecurity risk management program.
Several key aspects of the cybersecurity risk management program should be defined relevantto users of the report to assist with their understanding of the organization’s cybersecurity riskmanagement program.
The description criteria provides guidance of the relevant information for each of themain topics to be included below:
- Nature of the business and its operations
- Cybersecurity risk management program objectives
- Factors that have significant effect on inherent cybersecurity risk
- Cybersecurity risk governance structure
- Cybersecurity risk assessment process
- Cybersecurity communications and quality of cybersecurity information
- Cybersecurity risk management program monitoring
- Cybersecurity control activities
- Security event prevention management
- Security event detection and security incident response management
- Processing capacity management
- System availability management
- Confidential information management
By defining and documenting the above topics, organizations can provide vendors, businesspartners, management, and stakeholders with a reasonable understanding of the cybersecurityrisk management program in place. Users of the report can gain an understanding of thebusiness operations, challenging threats and vulnerabilities, control activities to address thosethreats, and procedures for responding if an event or incident occurs.
How it compares to the SOC suite
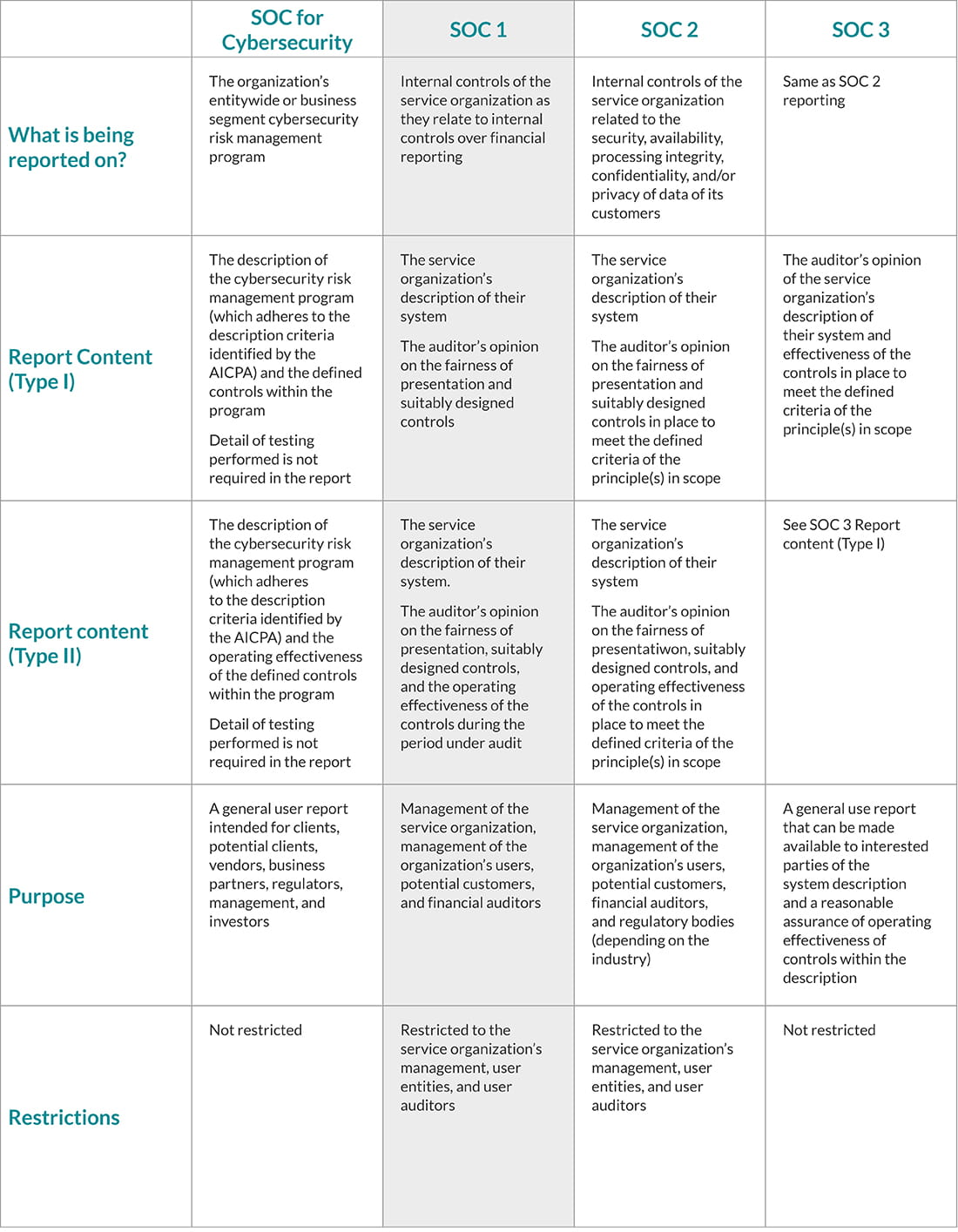
The new edition to the SOC Suite of reports allows for an industry agnostic examination forgeneral use. A SOC for Cybersecurity report defines the cybersecurity objectives and the riskmanagement program in place at an organization to meet those objectives. With the steadyincrease of cybersecurity attacks on small, medium, and large businesses, it is clear thoseaffiliated with organizations need to know what is being done to protect against cyber attacks.Understanding the cybersecurity objectives and its supporting risk management programprovides reasonable assurance and some peace of mind for business partners, vendors,customers, investors, regulators, and internal management. Most importantly, the SOC forCybersecurity allows for an independent third party to assess and issue an opinion. The opinionwould reinforce management’s description and showcase whether it is operating effectively.




