It’s not news that organizations have never been more vulnerable to data theft, manipulation, or ransom. Yesterday’s “trust but verify” cybersecurity paradigm is no match for networks that extend from your business into the cloud, into software-as-a-service providers’ servers, and even into your staff’s home Wi-Fi, cellphones, RFID chips, and smart watches.
Executives now recognize the never-ending threat posed by cybercriminals behind today’s AI-driven, automated hacking campaigns — and the damage they can do to customer loyalty, staff morale, reputation, and business continuity. It’s antiquated thinking to view cybersecurity breaches as IT problems; they’re business problems, and they should be treated that way.
Device connectivity, adoption of cloud computing, and the increasing sophistication, speed, and success of AI-driven automated hacking are making cybercrime easier than ever. Most recently, AI computing has enabled malicious actors to attack networks and devices at unprecedented speeds and levels of sophistication. With help from AI, attackers can almost instantaneously identify potential vulnerabilities, generate new attack processes to exploit them, and launch massive automated attacks.
Simply put: Modern, sophisticated, and ever-evolving cybersecurity threats require equally effective controls to prevent disruption and disaster. Enter Zero Trust.
What is Zero Trust security?
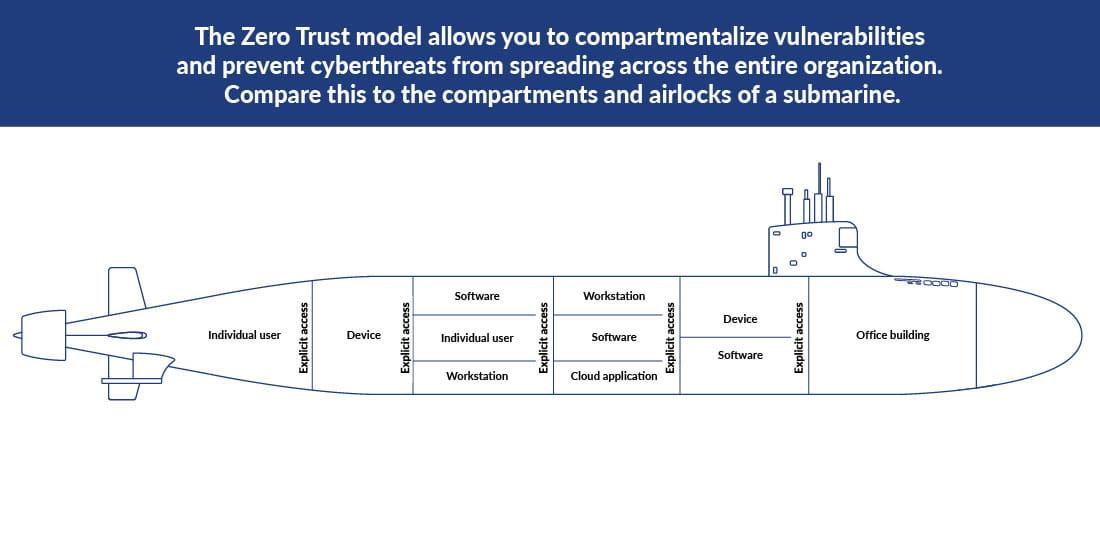
Unlike the familiar “trust but verify” model, Zero Trust is a “trust no one” model that assumes a breach has already occurred and restricts user access to digital assets and data on a need-to-know, just-when-needed, and where-needed basis.
It’s called Zero Trust because every user has to be authenticated, verified, and assigned a risk ranking every time they attempt to access the network or network resources. Ideally, every resource on the network — every user, device, application, and transaction — is continually challenged and validated to ensure that only authorized users with the appropriate risk ranking can access only the applications, services, or data they need, for only as long as they need to complete their task, and no longer.
The federal government recognized the importance of the Zero Trust model in 2021 amid nationwide lockdowns and the explosion of working from home. Executive Order 14028, “Improving the Nation’s Cybersecurity,” mandated baseline Zero Trust security standards for software sold to the federal government and required service providers to share cyber incident and threat information that could impact government networks, among other requirements.
The six pillars of Zero Trust
Most cybersecurity industry experts focus their Zero Trust initiatives on six “pillars:”
- Identity or user authentication
- Devices
- Networks
- Applications
- Workloads
- Data
How do these Zero Trust pillars work in the real world? Let’s say an accounts payable clerk (the user) typically signs into the company’s timecard database (authentication, data) and a payroll vendor’s web portal (authentication, application, networks) every other Monday at 9:00 a.m. (workloads) for about two hours from her desktop (device) remotely. In a Zero Trust framework, the clerk would be granted access to internal resources for just long enough to run payroll, only on alternate Mondays at 9:00 a.m., and only after their user ID, device ID, and location have been verified.
What if this clerk’s credentials are stolen, through a phishing attack or via malware like a keystroke logger? If a cybercriminal attempts to access the timecard database from a cell phone in the Philippines, at 11:00 p.m. on a Friday using the clerk’s credentials, a Zero Trust system could flag the behavior, time, device, and activity as atypical for a payroll clerk and lock that user ID out of the system pending further authentication and verification.
You’ve probably already experienced Zero Trust behavioral analysis yourself. Perhaps your debit card was locked after you attempted an unusually large purchase or if you tried to do a cash withdrawal outside your usual area. Those atypical behaviors are what a Zero Trust system looks for to evaluate a user’s risk profile and either allow or block activity on the network.
Five steps to implementing Zero Trust security
Zero Trust isn’t a software package, it’s a philosophy — and implementing Zero Trust is a lengthy process. Here’s how you can get started:
- Lead the change. Zero Trust isn’t just an IT initiative — it’s a cultural change that impact the way every staff member, supplier, and vendor interacts with your critical IT infrastructure. Work with your leadership team to educate staff about the vital need to improve cybersecurity and what to expect as your organization transitions to Zero Trust. Give your IT staff the authority and resources to succeed.
- Conduct an assessment. Start with your critical business needs. Understand what you need to protect in terms of data, applications, and services to keep your organization operating, and get a handle on where these assets are located.
- Map the transaction flows. Diagram how users interact with these vulnerable assets (also known as the “threat surface.”) Who needs access, why, when, and for how long? This process may be led by an objective outside Zero Trust consultant or an internal IT team working with other internal stakeholders to identify critical assets.
- Create organizational IT policies. These will regulate how internal and external users interact with critical assets. Pay particular attention to the granting of permissions to restrict users to just the access they need to complete tasks, and no more. Create policies that guide how your organization will react to — and recover from — a breach.
- Design a Zero Trust environment. Build your environment around the vulnerable assets, with the security protocols and policies as close as possible to the threat(s). This process will be different for every organization, as most will have to integrate existing legacy IT systems. Very few organizations can afford to take a “green field” approach and craft a Zero Trust system from the ground up. Then, on an ongoing basis, be sure to monitor your network, evaluate your incident response, and assess the suitability of new Zero Trust applications and technology. Implementing Zero Trust security is a process of continuous improvement.
The bottom line on Zero Trust
We operate in a profoundly interconnected, global IT landscape dominated by relentless, often automated cybersecurity threats. Leaders have a duty to clients, customers, and staff to protect the integrity of their IT systems and data, and in today’s cloud-based economy, that means Zero Trust architecture.
Implementing Zero Trust doesn’t necessarily mean burning your existing IT investment to the ground — very few organizations can withstand that kind of disruption. You can move toward Zero Trust tomorrow, simply by incorporating the Zero Trust philosophy and best practices into your existing software and processes and educating your people on the role they play in keeping the organization safe from cybercriminals. Put another way, getting started on your Zero Trust journey doesn’t have to cost anything.
Depending on your current IT infrastructure and overall environment, Zero Trust may not necessarily require a huge technology investment. But it does mean leadership, creativity, and flexibility are in order when implementing this new, more secure philosophy for interacting with cloud-based, connected digital resources.





