We see it time and again — an organization spends significant time and energy building their cybersecurity program and defenses but neglects to consider what they’ll do if their defenses fail. Even the strongest cybersecurity program isn’t 100% guaranteed to be breach-proof — that’s why you need to anticipate the worst and prioritize incident response planning with digital forensics. And because cybersecurity affects the entire organization, responding to a breach can't be just an IT task; executives need to be aware and involved.
The primary goal of planning ahead for a cybersecurity incident is to promote business continuity during a cyberattack and spend as little time as possible offline. An equally important goal is to make sure you can collect all the necessary data on the incident so you understand which data and systems were affected, identify the origin of the incident, and gather evidence properly so it can be used for legal, insurance, or compliance reasons. That’s where digital forensics comes in.
What is digital forensics?
Digital forensics, also known as computer forensics or cyber forensics, is the application of scientific processes to the identification, collection, examination, and analysis of data while preserving the integrity of the information through a strict chain of custody. Put simply, it’s a method of gathering digital evidence to uncover aspects of a digital investigation in a way that allows you to use it in court, present it to your insurance provider, demonstrate compliance, and so on.
When a suspected digital crime takes place within your company’s IT systems, proper collection of the digital evidence is necessary to shield your organization from liability. Investigation is necessary when you have (or suspect):
- Unauthorized use of information systems.
- Fraud committed by a staff member.
- A cyberattack by a hacker.
- Any breach of private or confidential data.
Even if your cyber event doesn’t require you to gather evidence for an external investigation, digital forensics is still critical to investigating the details of a cyber event and strengthening your cybersecurity defenses. Forensics can help you narrow in on the issue so you can determine the source of the cyber incident and focus on what needs to be investigated.
For example, you might find that only a specific version of your technology or a single workspace is affected. From there, you can shut affected systems down to prevent further damage and remedy the issue. Digital forensics also helps you to find exactly which data was compromised; if you don’t have this information, you won’t know what you need to recover. And if you don’t know how bad actors entered your system, you won’t know the weaknesses you need to address.
The digital forensics process
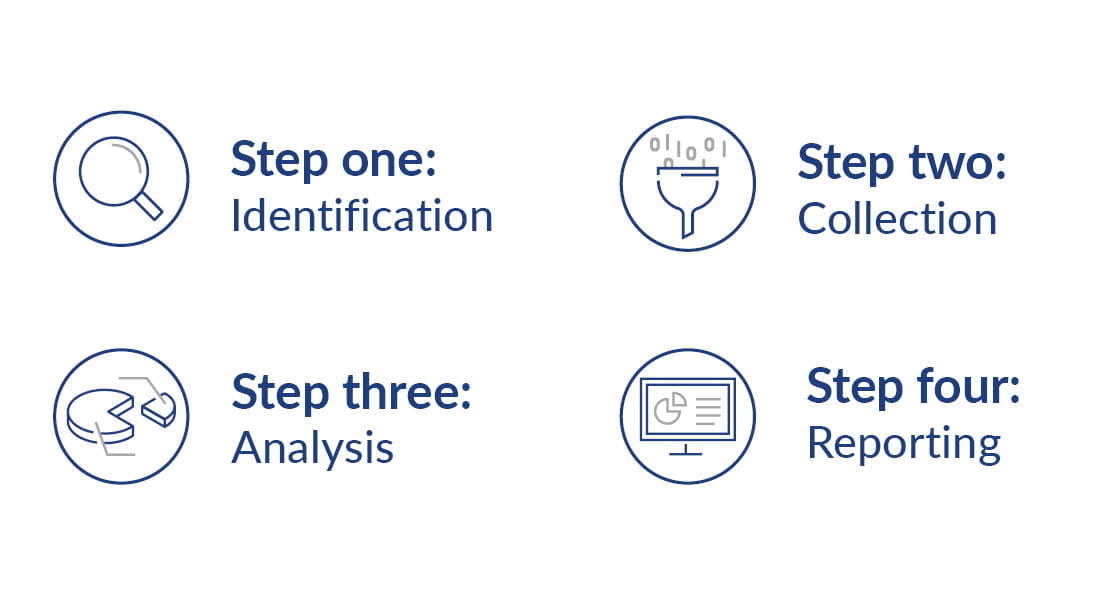
Given the often sensitive nature of situations that require digital forensics, you may need to call in experts. Here’s how the process typically works when you engage a forensic investigator.
1. Identification
Experts will work with your team to identify digital evidence for collection through a series of interviews regarding the events. Investigators will often interview you and your staff as well as outside parties like vendors.
2. Collection
The investigation team will determine a strategy for data collection and preservation, then collect the identified evidence to complete a forensic image. All analysis will be done with a copy of the forensic image to minimize the chances of unintentionally modifying the original evidence.
3. Analysis
The digital forensic evidence is evaluated and reviewed, and each data source, including vendor data, internal data, and other potential sources, will be evaluated to be included in the analysis. Investigators will work with you and your team to make sure any unique circumstances are considered.
4. Reporting
Investigators will create a summary report that can be shared with external parties and a detailed findings report for management reviewing the outcome of the investigation. In addition to presenting the facts of the investigation, they will outline any security considerations based on their findings to help you prevent similar cyber events in the future.
Plan ahead for digital forensics
When it comes to cybersecurity events, we always say that it’s not “if” a cybersecurity event will occur, but “when.” That’s why we put so much emphasis on helping clients prepare for the worst. Cyber criminals continue to find new ways to get around defenses, so you need to be ready to act in the event of an unauthorized activity, or worse, a data breach. When data needs to be handled in a specific way, it’s necessary to get it right the first time — or there might not be a next time. That’s why your incident response plan needs to include guidance for digital forensics, as well as a point of contact for a forensic investigator.





