In the world of cyber risk mitigation it’s no revelation that a logical “plan A” is preventing a cyberattack, while “plan B” is cleaning up the mess — and crucially — as quickly as possible. Time lost is money lost, and the longer it takes you to recover from a cyberattack, the more difficult it can be. An ounce of prevention may be worth a pound of cure, but when it comes to cybersecurity, prevention isn’t always possible. Too often, we see organizations put all their energy into preventing a cyberattack while neglecting to create an incident response plan for handling an attack they couldn’t prevent. Without a plan, they’re left scrambling to pick up the pieces and stop a business interruption — or worse.
Let’s dig into incident response planning so you can maintain business continuity, improve cyber resilience, and keep your people, processes, and technology protected, even when disaster strikes.
What is incident response planning?
“Incident response” refers to the actions an organization takes as a result of a threat to their cybersecurity. The incident could be as minor as someone scanning your IP range (the cyber equivalent of knocking on your door) or as serious as a successful ransomware attack. When these incidents occur, a swift and planned response is vital to business continuity and can mitigate additional cybersecurity risk, which is why incident response planning is so important.
An incident response plan is the predetermined list of steps your organization will take when a cyber incident occurs. It includes a list of members of the response team, stakeholders to notify like lawyers and third-party IT vendors, a digital forensics investigator, a communication plan, and other resources to help you minimize the damage of the incident. A strong, detailed plan will have a risk-ranking system, as it’s helpful in identifying what steps to take based on the type and severity of the cyber incident.
For example, if staff receive a phishing email, the incident response process may be as simple as documenting the incident and sending an organization wide notice to warn staff and remind them of phishing avoidance tactics. If a staff member clicks on the phishing email and a successful cyberattack occurs, the incident response steps may include shutting down affected systems, contacting clients whose data has been compromised, contacting your legal and insurance teams, having a digital forensics investigator evaluate and document the attack, and anything else it takes to stop the attack, resolve any issues, and get back to business.
Incident response plan development and roles
The complexity of your incident response plan can make a significant difference in how well it performs. In our experience, a fully developed incident response plan can take six months to flesh out, so at the very least, our experts recommend starting with a skeleton plan identifying roles and responsibilities. From there, running tabletop exercises on the plan will help you find opportunities for enhancements.
Identifying roles is one of the most critical aspects of incident response, and if you think IT is the only department that should be involved, think again. Strong incident response requires a variety of expertise, good coordination and communication, and significant leadership support. In addition to risk and compliance, HR, and IT representatives and other key stakeholders in the organization, executives need to understand and participate in cybersecurity incident response because these incidents can affect the entire organization.
To build your cyber incident response team (CIRT), you’ll first need to identify a CIRT lead. A common choice for a CIRT lead is the leader of the IT team; however, it’s important that this person isn’t too involved in day-to-day IT activities. The CIRT lead shouldn’t be the same person who will be in your IT systems investigating and fixing the issue — that person needs to stay focused on the technical aspects of resolution. For this reason, the CISO or other C-level executives are often considered as lead. Whoever the CIRT lead is, they need the trust of leadership, deep knowledge of your organization’s structure, and risk management skills.
The rest of the team should include leaders from HR, IT, legal, operations, marketing, and any departments of the organization you think could be helpful. You’ll need somebody to coordinate communications with stakeholders, someone to lead repairing of IT systems, and someone to investigate the issue. You’ll also want third parties identified as part of the plan, including external legal counsel, insurance, digital forensic investigators, and IT.
Business continuity and other benefits
It’s almost impossible to name a business that can operate while their technology is failing, which is why incident response planning and business continuity planning (BCP) are so closely tied together. Cybersecurity breaches can shut down your IT systems, leaving you unable to perform critical business functions like processing transactions, accessing vital data, operating machinery, or even receiving emails. How long can your business survive without technology? If you don’t have a plan for responding to a cyber incident, it’ll take much longer to bring your technology back online. A good incident response plan will help you minimize the time and resources it will take to mitigate a cybersecurity breach. It also maximizes your chances of a full system recovery and return to business as usual.
Another benefit of incident response planning is the ability to quickly recognize, document, and resolve an issue so that you can demonstrate to external parties that you’ve taken appropriate action. This can be vital to avoiding legal culpability and capturing recoverable costs with your cyber insurance coverage. Note that you may need to engage digital forensic investigators to get the incident documented in a manner presentable in court.
If the incident gets media coverage, you’ll be very glad you handled the issue quickly and responsibly rather than taking a reactive approach where emotional decisions are made. Cybersecurity issues can be devastating to an organization’s reputation and public image if handled poorly.
Six steps of incident response planning
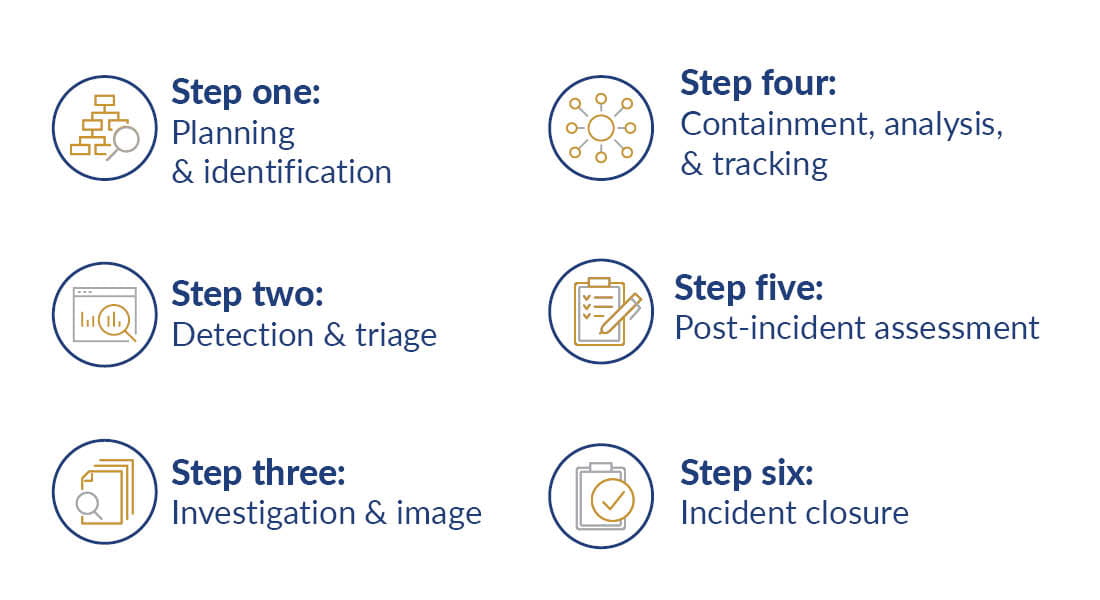
It’s common to work with third-party experts to develop an incident response plan. While you don’t have to follow these exact steps, this is a flexible framework on how we advise clients to structure their incident response plans.
1. Planning and identification
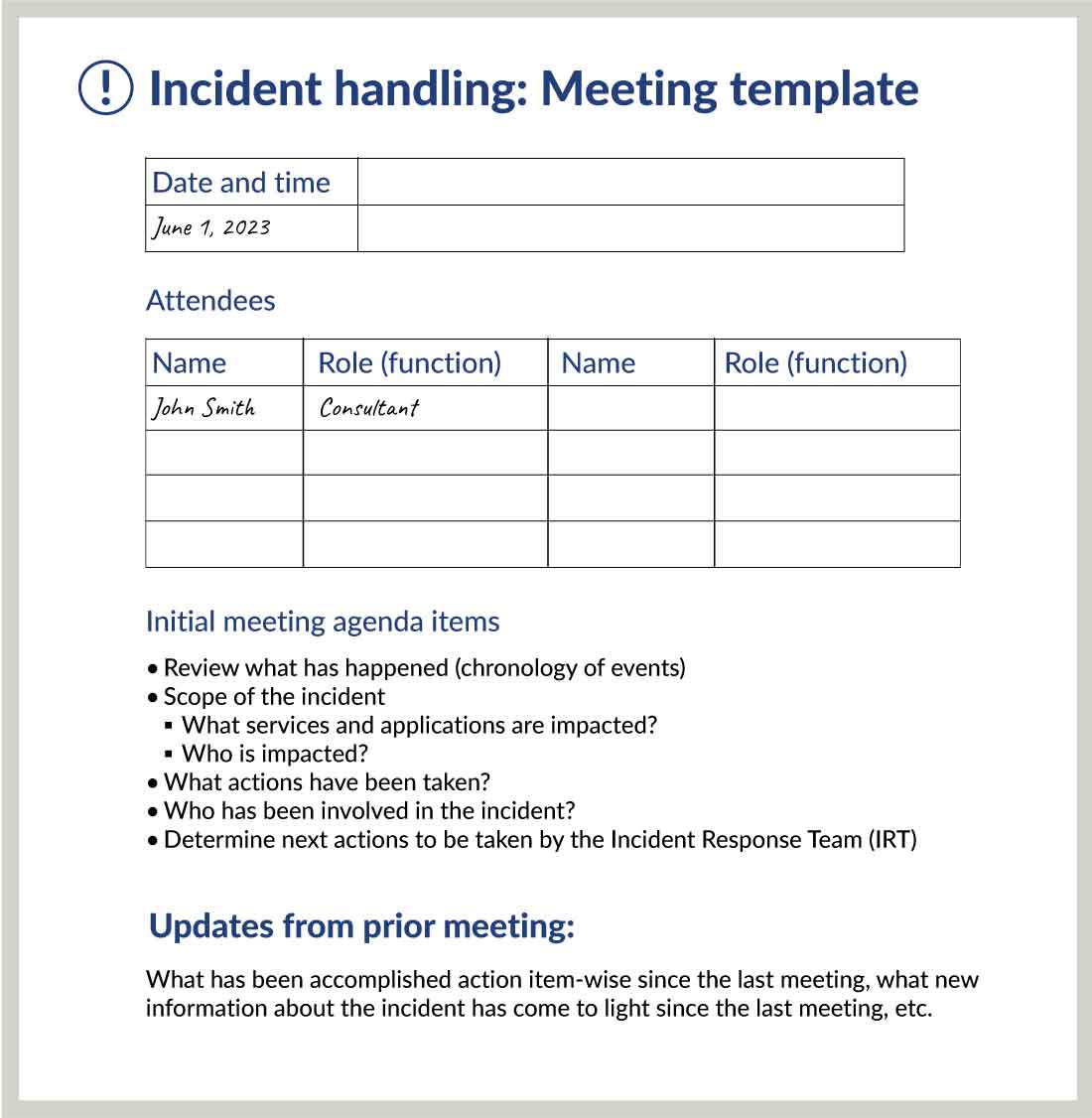
The first step when responding to an incident is identifying the incident type and determining the course of action. This part of the plan should include a risk-ranking assessment to help determine next steps along with a communication plan outlining who to assemble to address the issue and stakeholders that need to be notified. We advise creating templates for certain things ahead of time so no steps are missed — for example, an agenda for the initial meeting, a chart for determining roles and responsibilities, drafts of communications, and outlines for documenting lessons learned after the event.
2. Detection and triage
Next, you’ll need to identify the extent of the damage to information systems as well as personnel and accounts involved in the incident. This part of the plan needs to include how you’ll detect an incident and how you’ll classify it. Typically, incidents have three classifications: nuisance, high, and critical. It’s important to understand what detection technology you have in place and who will be responsible for analyzing and classifying the incident.
3. Investigation and image
Once the extent of the security incident is known, you’ll need to investigate and analyze the breach to determine the root cause, potentially with assistance from forensic investigators, cybersecurity professionals, and cyber insurance agents. Your plan should include guidelines for how you'll identify the origin of the attack, the timeline of events, and the potential impact zone. Identifying and collecting things like compromised security logs can be helpful for additional analysis, and you may want to refer to them later. Working with a third-party forensic investigator to get a forensic image is especially important if you need a defensible data set to use in a legal or insurance situation.
4. Containment, analysis, and tracking
After you’ve conducted the investigation, you'll need to start the containment process to prevent further damage. Your incident response plan will ideally include business continuity or disaster recovery plans to help you keep interruptions to a minimum.
The process of containment, analysis, and tracking is where you begin to identify where the cyber event might have occurred, and you can continuously narrow until you isolate the issue down to the specific workstations, users, and data affected. You’ll conduct analyses to verify and validate your findings, track the extent of the incident throughout the organization, and the initial event that led to the cyber event or system compromise.
5. Post-incident assessment
Following incident analysis and containment, you’ll complete a post-incident assessment to identify corrective actions and record how successfully the response and recovery efforts were conducted. Having templates for documenting your process, lessons learned, and areas for plan improvement will fortify your incident response plans. You’ll want to include space to answer questions like, where did we excel? What gaps were in our plan? Did we need more external support? Did we actually follow the plan, or did we throw it away after day one? This is your opportunity to improve how you handle future incidents.
6. Incident closure
Make sure your plan includes guidelines for formalizing your post-incident assessment. During the incident closure process, you’ll create a document summary of the events, your corrective action, your control gap recommendations, forensic report, and anything else your stakeholders need to know. Note who will need summary documents and what needs to be included based on the audience. For example, your board of directors will likely need a different, more high-level version of the summary than your IT department, and you may need additional versions for lawyers, insurance companies, and auditors.
Get started with incident response planning
The most effective way to start with incident response planning is to identify the key members of your CIRT. This team can create a skeleton plan outlining key contacts, initial action items for each role, and business continuity plan basics. (For example, if you lose the ability to send or receive emails, will you default to a different system? If that goes out, can staff use their personal phones?)
Once you have a plan outline, run your tabletop exercises using different scenarios to discover where you need more robust planning, which contacts need to be added to the list, and whatever else you find to be missing.
Remember: The longer the recovery from a cyberattack, the more severe the consequences. Cyber criminals won’t wait for you to be ready, so now’s the best time to prepare.





