It might start with an avalanche of help-desk tickets because your staff can’t log onto their desktop computers, or perhaps your plant manager encounters an equipment shutdown for no discernible reason. The probable culprit in these examples? A cybersecurity attack, and more likely today than ever, ransomware.
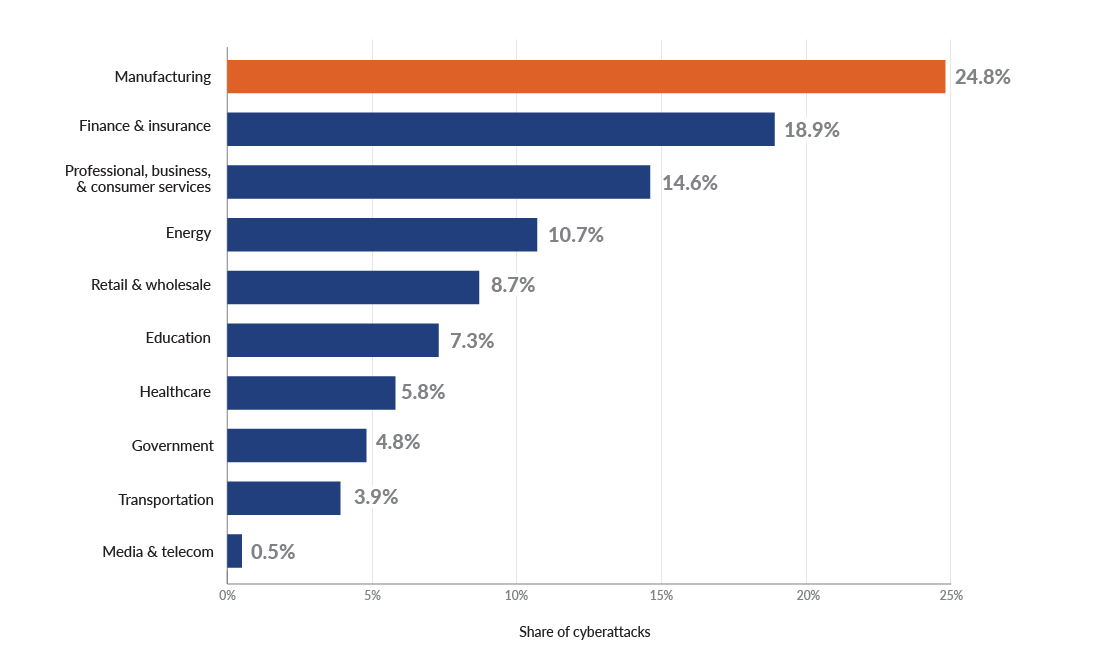
According to Statista, the manufacturing space had the dubious distinction in 2022 of experiencing the greatest percentage of cyberattacks among top industries globally — ahead of finance, insurance, and healthcare.
Many times, the breach occurs after access to your system is granted through a social engineering ploy. Often the purpose is to perpetrate financial fraud. For instance, attackers might spoof a phishing email, an impersonated message that looks just like it came from your controller. When the unsuspecting recipient, perhaps a staff in your department, receives the email, they follow instructions and update payment account information. Guess where your funds now go?
What is ransomware, and how does it impact manufacturers?
Perhaps the single most important reason manufacturing leaders should be extremely concerned about the cybersecurity measures they take — or, unfortunately, often don’t take — is ransomware. In the past, cybercriminals “only” encrypted your data until you paid their hefty ransom. But ransomware has become big business for cybercriminals, and their tactics are changing.
Today, bad actors sometimes perform double extortion. Not only do they hold data for ransom; they also threaten to sell or publish the information extracted from the network if a company refuses to pay.
It’s not uncommon for manufacturing businesses that fall prey to ransomware to be attacked two or more times. Adversaries who successfully breach your system’s defenses share their "wins” on the dark web, selling other cybercriminals information about how they got into your system. The risk isn’t only data theft and access to confidential information but the criminals’ ability to create back doors into your environment for their so-called “customers” to later exploit.
Cybercriminals may hang out in your system for a while, doing the digital equivalent of putting their feet up on your network’s couch. They can remain undetected, lurking for weeks or months. One manufacturer recovered its environment after a ransomware attack — at least it thought it did — only to find many weeks later that the hackers were still inside. While there, they had wiped out the company’s backups, including years of financial records that had to be painstakingly reconstructed from paper records.
Operational technology and manufacturing cybersecurity
Operational technology (OT) can give hackers an entirely new level of opportunity and power over manufacturers. With the increase in automation, smart manufacturing, and Industry 4.0 technologies, more and more plant floor equipment is controlled by computers and internet connectivity. Bad actors no longer have to encrypt your data to hold it for ransom; they can launch a denial-of-service attack that shuts down your operations.
And if, like a lot of manufacturers, you’re running old technology, your OT is potentially even more vulnerable than your IT. The situation is further compounded by blurred lines of responsibility and risk ownership — although your production lines connect to your IT network, they’re usually not managed by your IT team but rather, engineering.
Meanwhile, although cybersecurity impacts the entire business, it typically sits under the IT umbrella. But IT is not cybersecurity. IT’s job is to facilitate access to information; cybersecurity’s job is to protect it. Multifactor authentication (MFA) is a good example. It might be inconvenient to take that extra time and step to log in, but MFA is a sound security control.
It’s a delicate balancing act. So, when your IT team tells you they have cybersecurity covered, trust but verify. Because without dedicated resources and direction from the top of the organization, you won’t have the mindset required to protect your business from a cyberattack.
Why are ransomware attacks on manufacturers rising?
Additional factors make manufacturers an increasingly common target of cyberattacks and especially ransomware. Take the low tolerance for downtime, a manufacturer’s greatest risk. With just-in-time contracts and many facilities running at more than 100% capacity, lost production time can’t be made up. When you consider that ransomware attacks take organizations down for more than three weeks on average, you don’t want to do the math on lost production.
The low tolerance for downtime and running older unsupported legacy systems is also why patching known vulnerabilities often falls behind. A high proportion — 76%, according to Ivanti — of recent attacks have exploited a known vulnerability.
Additionally, it’s an unfortunate reality that IT and cybersecurity spend tends to track toward compliance, and unlike in banking, finance, and healthcare, manufacturing doesn’t have similar regulatory and compliance requirements for cybersecurity. As a result, most manufacturers lag in their cyber investments; many don’t have anyone in their organization solely focused on cybersecurity, making them prime and easy targets.
Prioritizing manufacturing cybersecurity
Let’s cut to the chase: Too many manufacturers are failing to take the steps needed to prevent a cyberattack, including major disruption caused by ransomware. They’re not hardening remote access. They lack the right endpoint protections. Their detection and response capabilities are lagging. Too often, their backups are vulnerable, too.
Just in case you’re operating under the assumption that cyber insurance will enable you to recover your losses after a cyber or ransomware attack, stop. Consider that, without following current best practices, it’s becoming increasingly difficult to meet insurers’ requirements for coverage. Or, if you are approved, you’ll be subject to higher premiums for less benefit.
It’s critical to be proactive; hackers certainly are. Do you know where the threats and vulnerabilities lie in your organization? Risk assessments and penetration testing are two types of verification that can uncover gaps before cybercriminals expose them for you.
The cost of prevention is far less than the costs of recovery after a breach — and the costs of lost production. Don’t put your manufacturing business’s ability to operate at risk.





